We show you the possible signs
Unlike Android, iOS devices (iPhone, iPad, and iPod touch) are less susceptible to malware infections or hacks. But they aren’t immune to malware attacks.
This guide will show you some warning signs that a hacked iPhone displays. You’ll also learn how to improve your device’s security. If your iPhone exhibits any of the symptoms below, it’s probably been hacked.

What Are the Signs of Your iPhone Being Hacked?
iPhone hacks exist in different forms, and there’s no one way to test for them all. You have to manually look out for specific symptoms or abnormalities like the ones below:
- Unrecognized Apps or Incessant Pop-Ups: A malware hack or infection could cause your iPhone to display incessant pop-ups and install unwanted apps without your knowledge.
- Battery Drained: Does your iPhone battery die faster than usual? It could be due to increased background activity of malicious software.
- Performance Lag: Rogue apps will overwork your iPhone’s CPU and consume excessive memory space, resulting in performance lag and other issues.
- High Data Usage: Some malicious software exchanges information with their developers round-the-clock over the internet. Hence, a sudden spike in mobile day usage is a valid indicator of a phone hack.
- Suspicious Phone Calls, Text Messages, and Notifications: Does your iPhone send automated text messages to unknown phone numbers? Are there random outgoing calls in your call log? That’s a clear indication that your iPhone is hacked.

How Do iPhones Get Hacked?
The primary purpose of a hack is to access data on your device. Hackers typically employ malicious software (viruses, spyware, etc.) to obtain information from your iPhone fraudulently.
Apple does a great job of preventing fraudulent developers from uploading malicious apps to the App Store. So, it’s almost impossible to install malware from the App Store. However, the following activities can expose your iPhone to security threats and invasions:
- Jailbreaking Your iPhone: If you download apps outside the Apple App Store on a jailbroken iPhone, the chances of malware infection are much higher.
- Using Public Wi-Fi: Cybercriminals often exploit public Wi-Fi networks to spread malware, infiltrate people’s devices, and steal sensitive data. If you don’t want to get hacked, staying away from public Wi-Fi is an excellent place to start.
- Running Outdated Operating System: Failure to install software patches or updates exposes your iPhone to new security threats.
- Poor iCloud Security: If hackers get hold of your Apple ID account login information, they have direct and indirect access to your iPhone. They can change your account password, access your iCloud backup, or remotely erase your iPhone.
What to Do When iPhone Has Been Hacked
Here are some tips to end an ongoing hack and prevent its reoccurrence in the future.
1. Disable Data Usage for Suspicious Apps
A lot of malware runs quietly in the background, sending personal data to the hacker or developer from your iPhone. Some malware even install spyware and other types of malware on your device.
Malware activities are often data-intensive. If you exhaust your limited data plan faster than usual, or there’s a sudden spike in your phone bill, check your iPhone’s data usage for unfamiliar apps responsible for the problem.
Go to Settings > Cellular (or Mobile Data) and scroll to the “Cellular Data” or “Mobile Data” section.
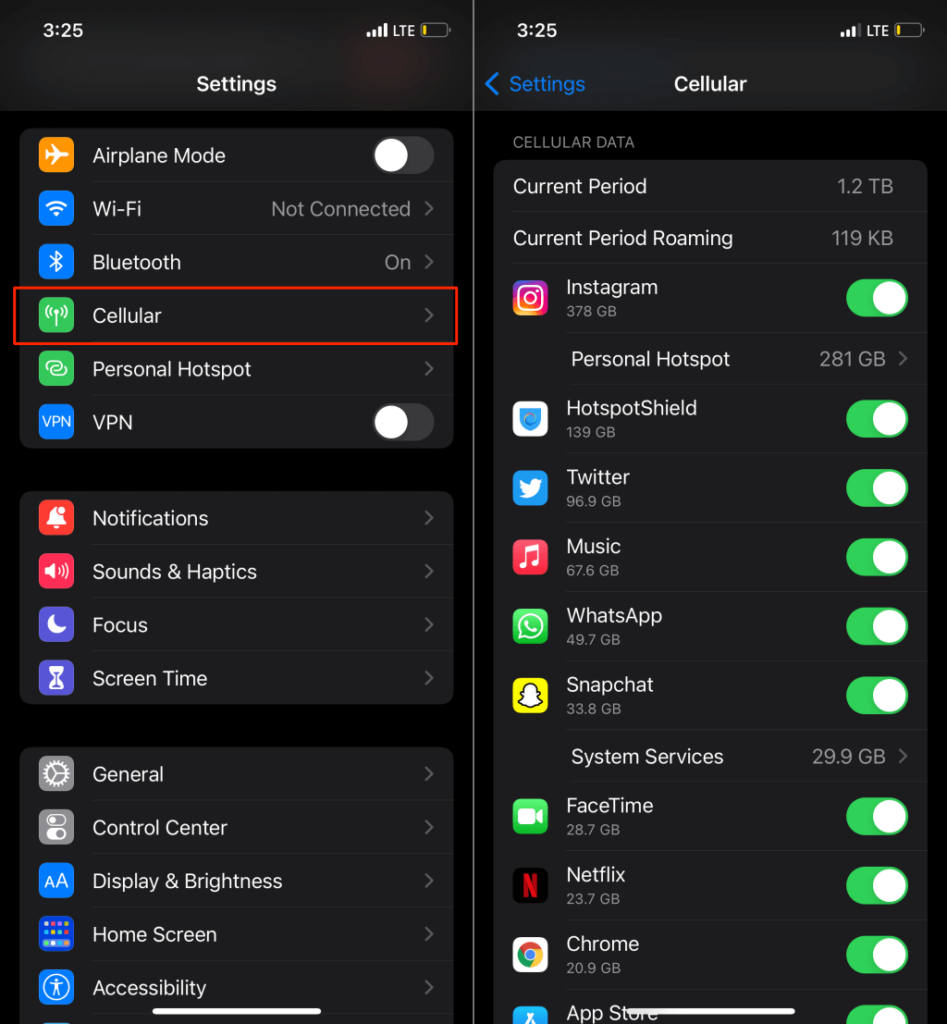
Apps are arranged in descending order of data consumption. Disable cellular data access for unrecognized or phony apps and monitor your iPhone’s data usage and behavior afterward.
If data usage remains unusually high, refer to our guide on reducing data on iPhone for more troubleshooting tips. Additionally, confirm that your iPhone doesn’t have any spyware.
2. Check CPU and RAM Usage
Excessive CPU and memory usage by rogue apps will overheat your iPhone and slow its performance. These apps often run constantly in the background, using up system resources and overworking your iPhone.
There’s no native method to check your iPhone’s CPU usage. However, reliable third-party apps (free and paid) in the App Store can get the job done. Refer to our tutorial on monitoring RAM and CPU on iPhones for more details.
If no unrecognized apps are using your iPhone’s CPU or RAM, try other known tricks that can help cool down your device. Remove your phone case, disable background app refresh, unplug your charger, reduce the screen brightness, etc.
We also recommend reading this article that highlights 15 maintenance tips to keep your iPhone running smoothly. The recommendations in the article can speed up your iPhone’s performance tremendously.
3. Check Your Battery Usage

Background malware activity can also result in increased battery drainage and other battery-related issues. Luckily, iOS analyzes the amount of battery power each app uses on your iPhone. So, it’s easy to trace any malware responsible for the battery drain problem.
Go to Settings > Battery and wait a few seconds for iOS to load the battery usage report. By default, iOS displays app battery usage for the last 24 hours. Head to the Last 10 Days tab to view a cumulative battery usage report for the past ten days.
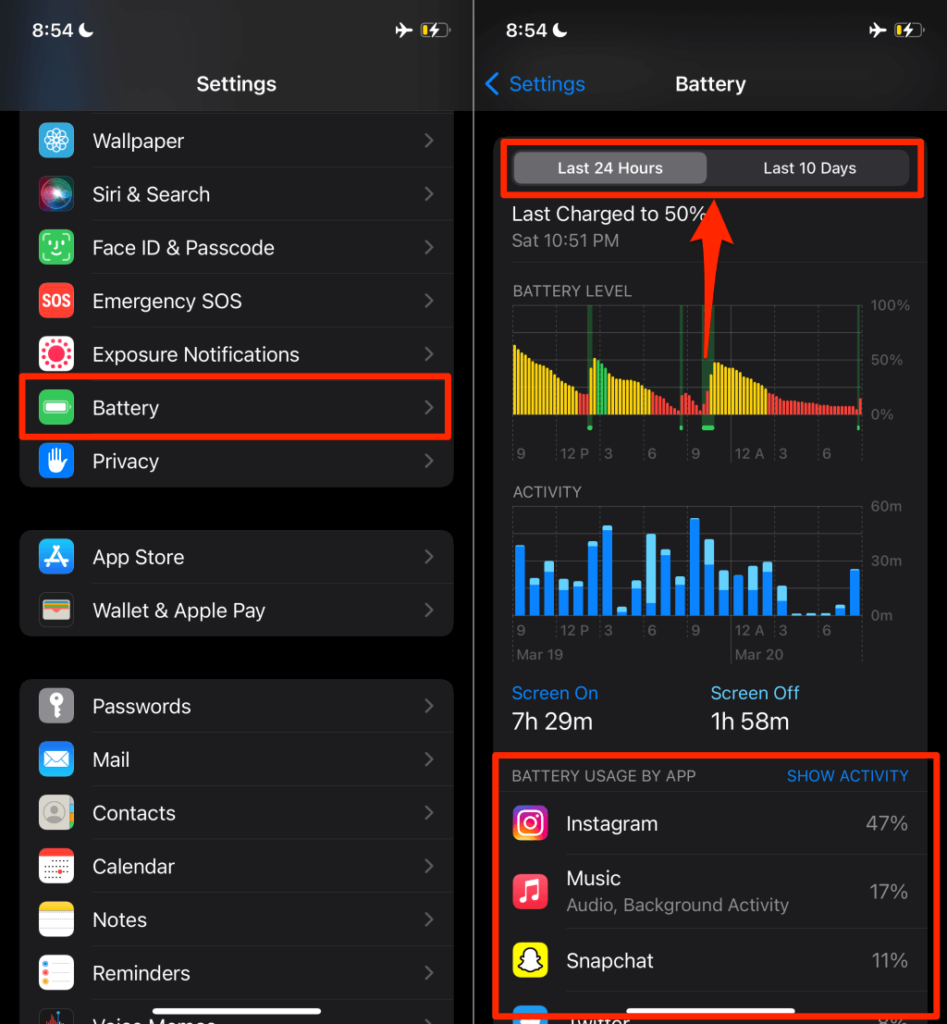
Tap Show Activity above the first app to view each app’s on-screen and background activities instead.
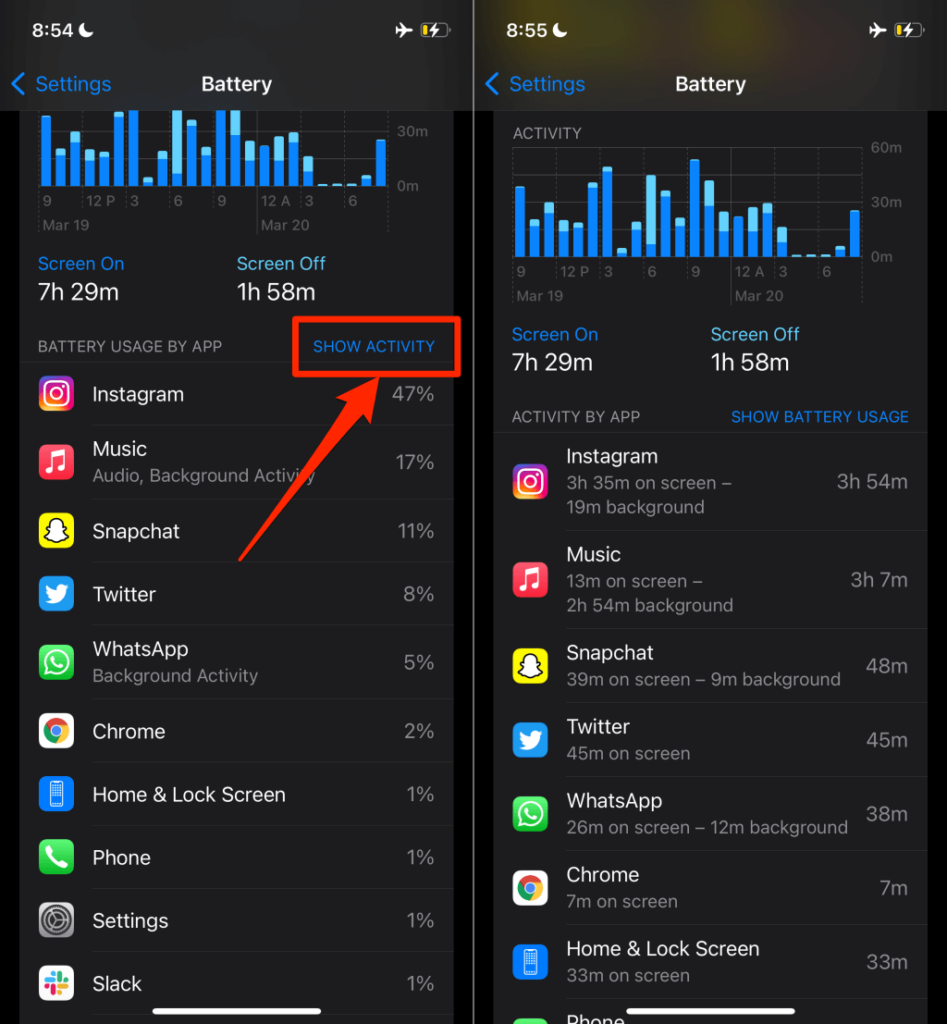
Go through the list carefully and note any unrecognized or strange apps with high background activity and battery usage. Jump to the next section to learn how to remove the suspicious apps from your iPhone.
4. Uninstall Suspicious Apps
Delete any unrecognized app with an insane amount of data consumption, battery usage, or high background activity—especially if it’s an app you barely use.
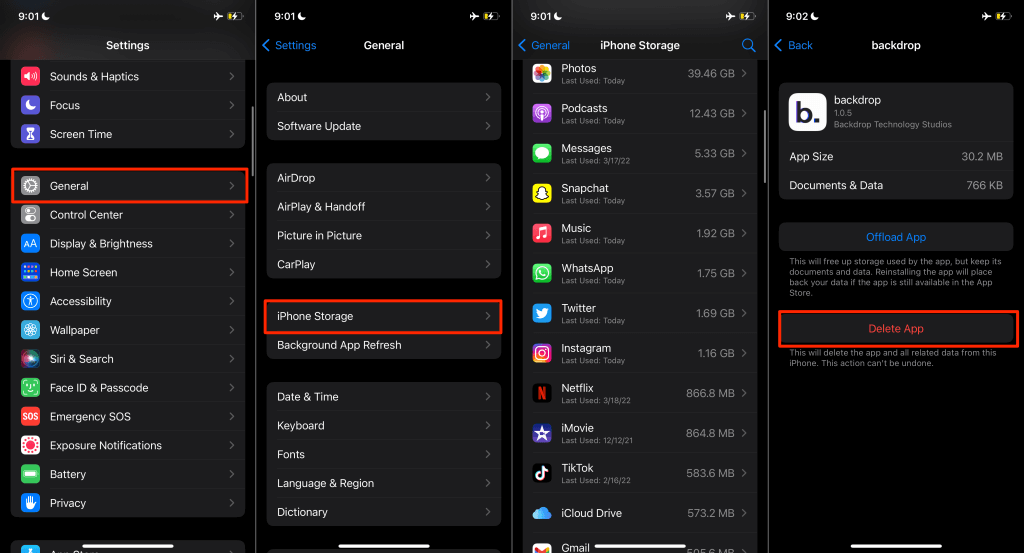
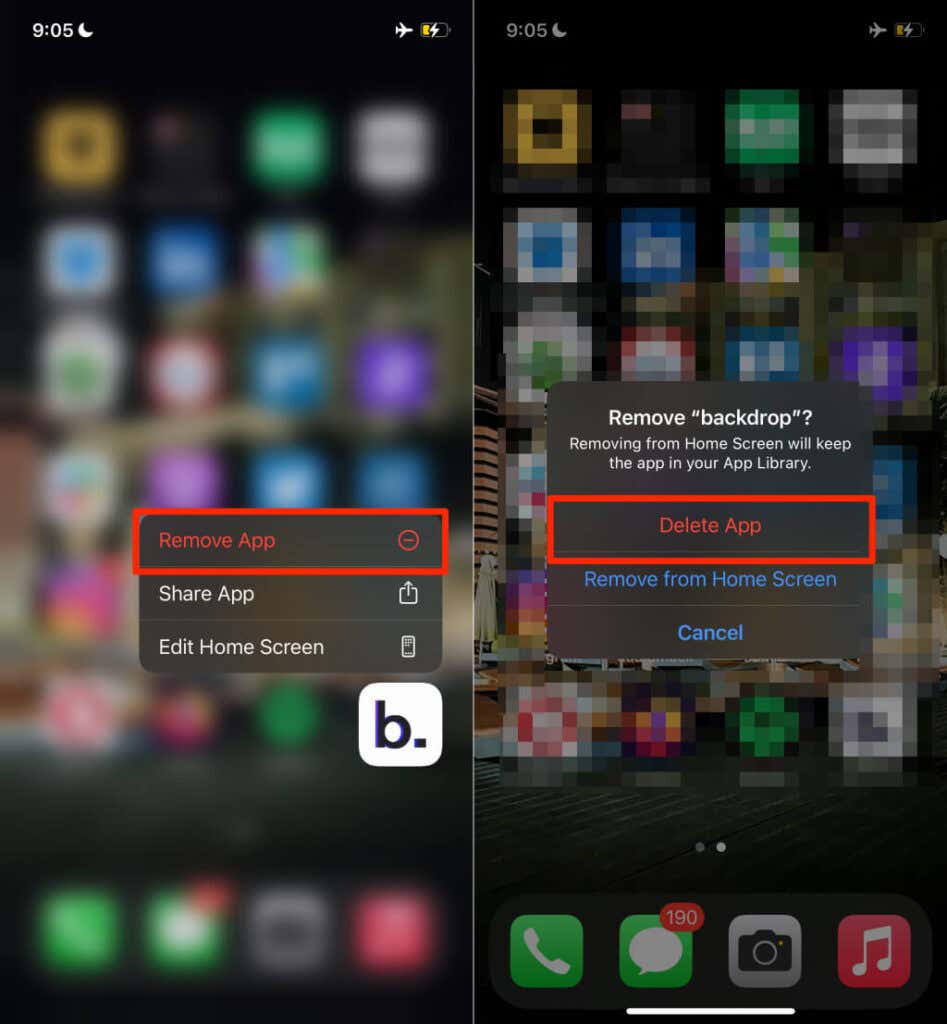
Head to Settings > General > iPhone Storage, select the app, tap Delete App, and tap Delete App again on the prompt.
Alternatively, long-press the app on the Home Screen, tap Remove App and select Delete App on the confirmation prompt.
5. Restart Your iPhone
A simple device reboot might eliminate temporary glitches that seem like a hack or malware attack. For example, if your iPhone dies quickly, but there’s no suspicious app in the battery usage report. A reboot could fix the problem.
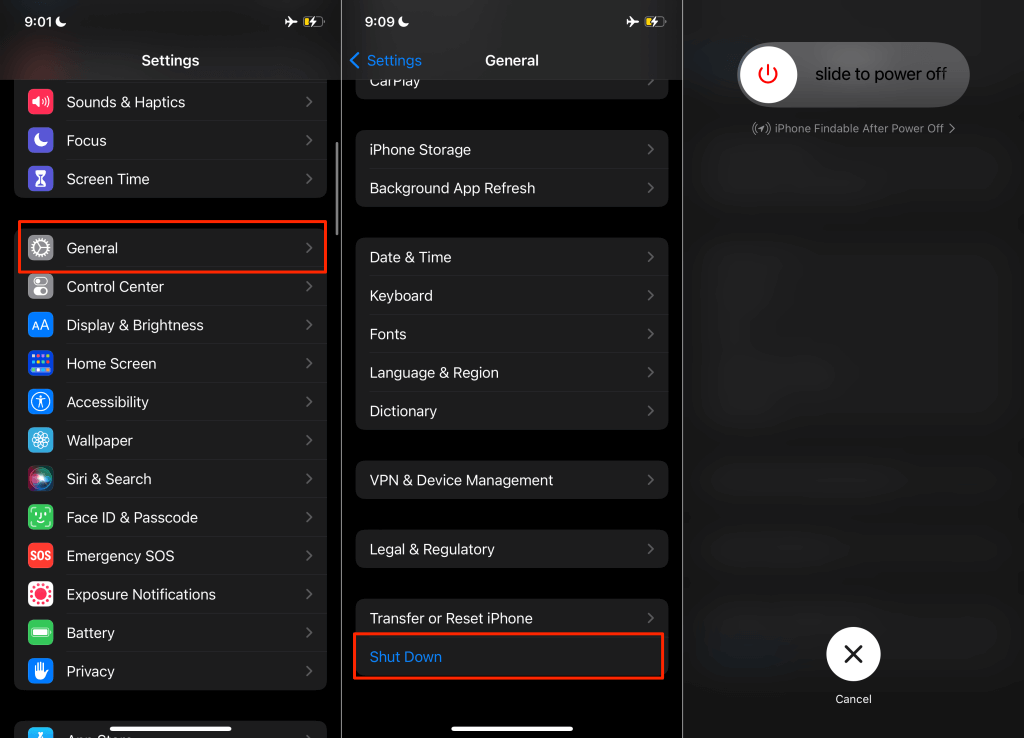
Go to Settings > General > Shut Down, drag the slider, and wait 30 seconds for your iPhone to shut down completely. Afterward, press and hold your iPhone’s Side button until you see the Apple logo.
6. Update Your iPhone
iPhones running outdated operating systems are more vulnerable to all forms of attacks. For instance, the iOS 14.4 and iPadOS 14.4 updates fixed issues that allowed malicious applications to access and leak sensitive information on iPhones and iPads. iOS 14.3 and older also had vulnerabilities that allow an attacker to access private contact information on your iPhone—even when locked with a passcode.
Apple and some third-party security companies spot vulnerabilities that hackers can exploit and (Apple) release security patches to block them. That highlights the importance of updating your iPhone.
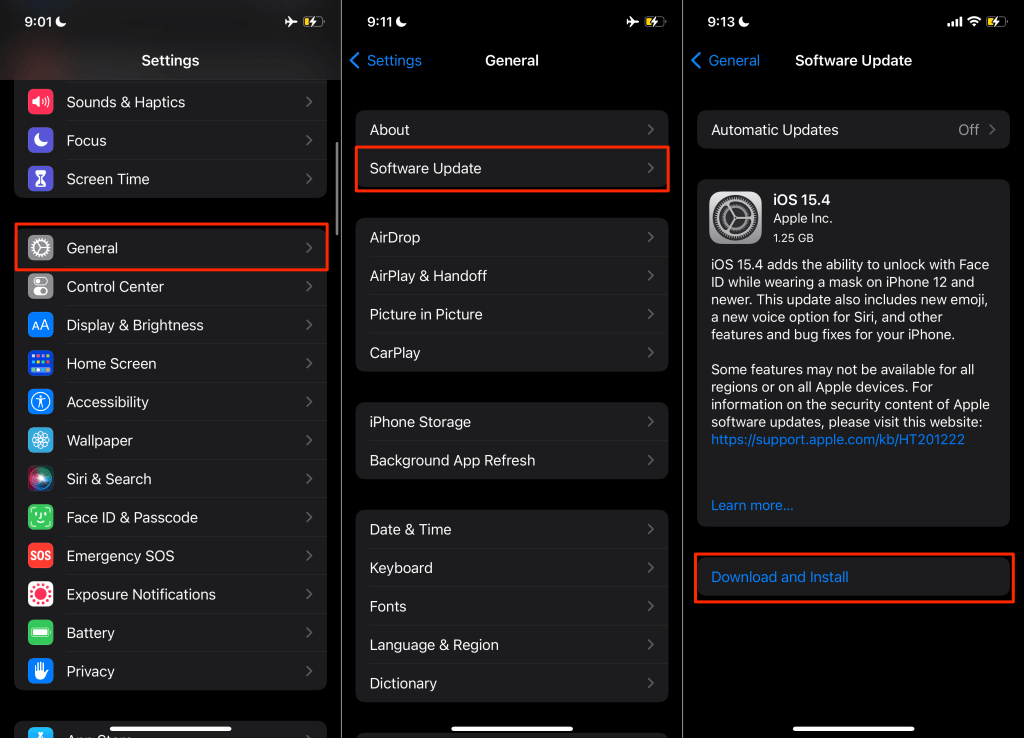
Open the Settings app, select General, tap Software Update, and tap Download and Install to update your iPhone.
7. Avoid Public Wi-Fi Network
Public Wi-Fi networks barely have solid security systems. That makes it easy for a hacker to intercept exchanges on websites you visit while using the network. Some hackers even set up fake public Wi-Fi networks that mimic genuine networks.
Joining such Wi-Fi networks allows hackers to access your internet traffic personal data like credit card information, passwords, etc. If you have to use public Wi-Fi, do so with a Virtual Private Network (VPN). VPNs will secure your connection by masking your IP address and encrypting data exchanged on the network.
8. Secure iCloud with Two-Factor Verification
If hackers gain access to your iCloud account, they have everything you’ve uploaded from your iPhone to iCloud. In addition to using a strong password, secure your Apple ID account with two-factor authentication.
9. Factory Reset Your iPhone
Erase your iPhone and reset it to factory default if it continues to exhibit signs of malware hack.
Go to Settings > General > Transfer or Reset iPhone > Erase All Content and Settings. Tap Continue and enter your iPhone’s passcode to proceed.
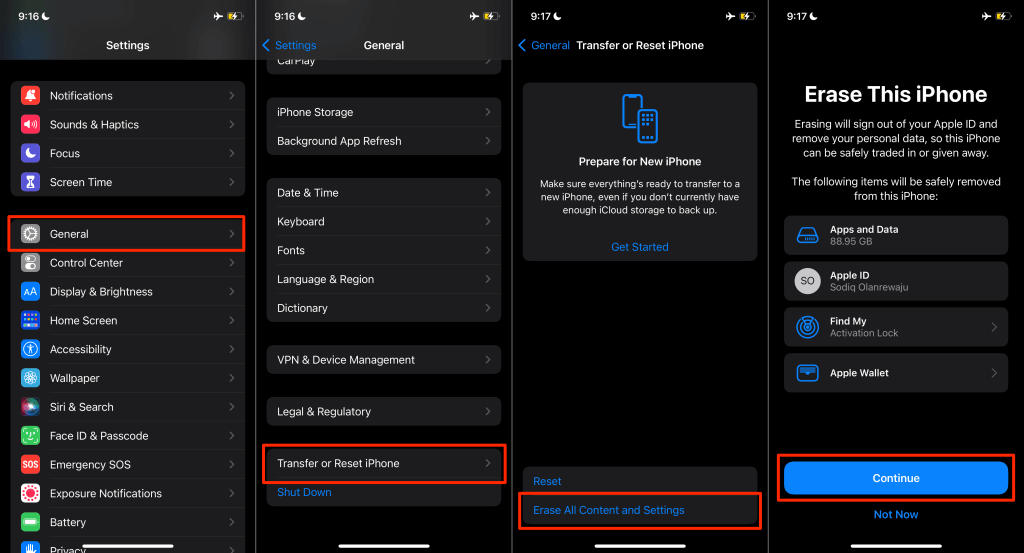
On iOS 14 or older, go to Settings > General > Reset > Erase All Content and Settings.
Keep Your iPhone Hack-Proof
iOS runs applications in a sandboxed environment, so it’s almost impossible for malware to spread across other apps—unless you jailbreak your iPhone. But to reiterate, iPhones aren’t immune to security threats or hacks. However, you now know what to do if your iPhone exhibits any of the abovementioned signs. Contact Apple Support if the issues persist.




